4/4/19
Finding that using these commands on a daily basis help me troubleshoot issues and just wanted to share:
netstat -f = this command tried to resolve every connection to their FQDN
netstat -r = this command show the local routing tables on the PC
netstat -a = show all active TCP/IP connections on the PC
netstat -e = this shows any errors on the network adapters or lost packets
ping -t = this allows for a constant ping of an address
ipconfig = this show basic network configuration of the local adapter
ipconfig /all = this shows every detail about all network adapters on the local PC
arp -a = this show the mac address table on the local machine for the devices it’s “talked” to on the network and has saved in memory. Once you reboot this table clears.
nslookup [internal IP or external IP or FQDN] = this commands allow me to resolve internal or external dns names to see what address come back, if the response on local addresses comes back with a :unknown: this means that reverse DNS lookup is not setup.
Useful command on checking to see if a networks DNS server is secure:
- type ‘nslookup’
- type ‘DNS servers IP address]’ and press enter – cheat: do a nslookup [name of the local domain if you hover over the network adapter on the Windows desktop and this will reveal the local DNS server IP address]
- type ‘set type=any’ and press enter – note: notice no spaces
- type ‘ls -d [domain name] – [domain name is the name of the domain that you found in the hint in #2 above or any public domain like google.com as an example]
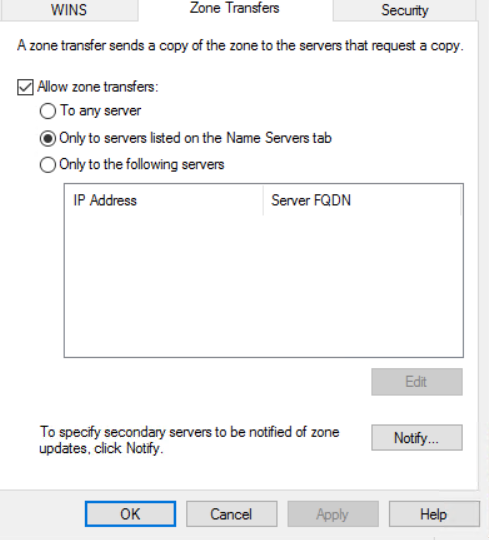
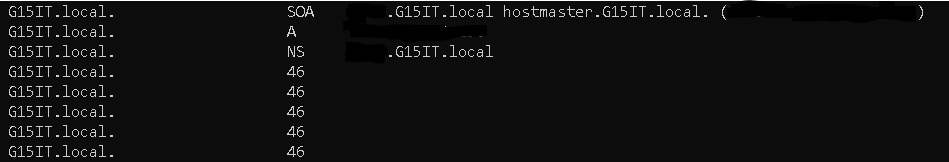
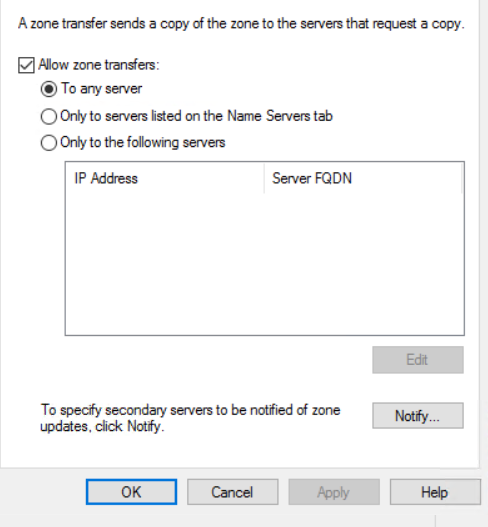
- If this comes back with the SOA, NS, A, and MX records then this domain is allowing zone transfers and this is BAD! – it means I could redirect DNS to a rogue DNS server
Below is an example of what a blocked zone transfer looks like in a mock DNS server in the lab.
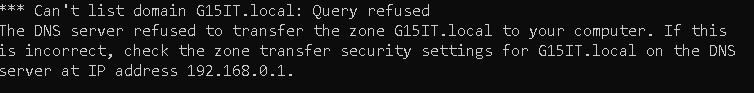
Zone Transfer Blocked!
Useful Website for looking up the security of a public website:
https://tools.pingdom.com/#5a7a0a61d8000000
I hope this little write up is helpful to some. 🙂
Always-be-Labbing!
~Trevor