Created: 1/24/23
Updated: 1/24/23
The following are the steps to set up Advanced Audit Policies in your Domain controllers to allow Defender for Identity to collect the proper audit logs to function properly.
Reference: https://learn.microsoft.com/en-us/defender-for-identity/configure-windows-event-collection#configure-audit-policies
- Log in to the server as Domain Administrator.
- Open the Group Policy Management Editor from Server Manager > Tools > Group Policy Management.
- Expand the Domain Controllers Organizational Units, right-click Default Domain Controllers Policy, and then select Edit.
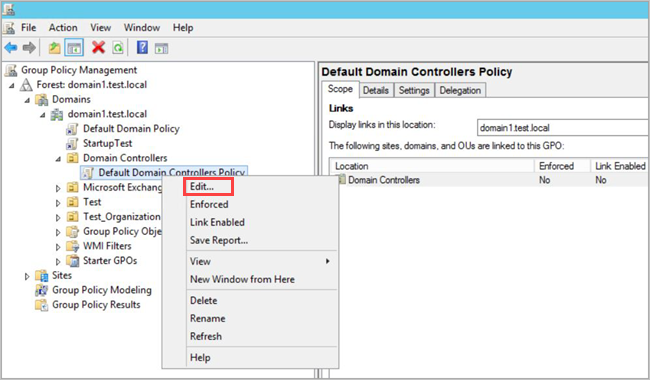
- From the window that opens, go to Computer Configuration > Policies > Windows Settings > Security Settings and depending on the policy you want to enable, do the following:
For Advanced Audit Policy Configuration
- Go to Advanced Audit Policy Configuration > Audit Policies.
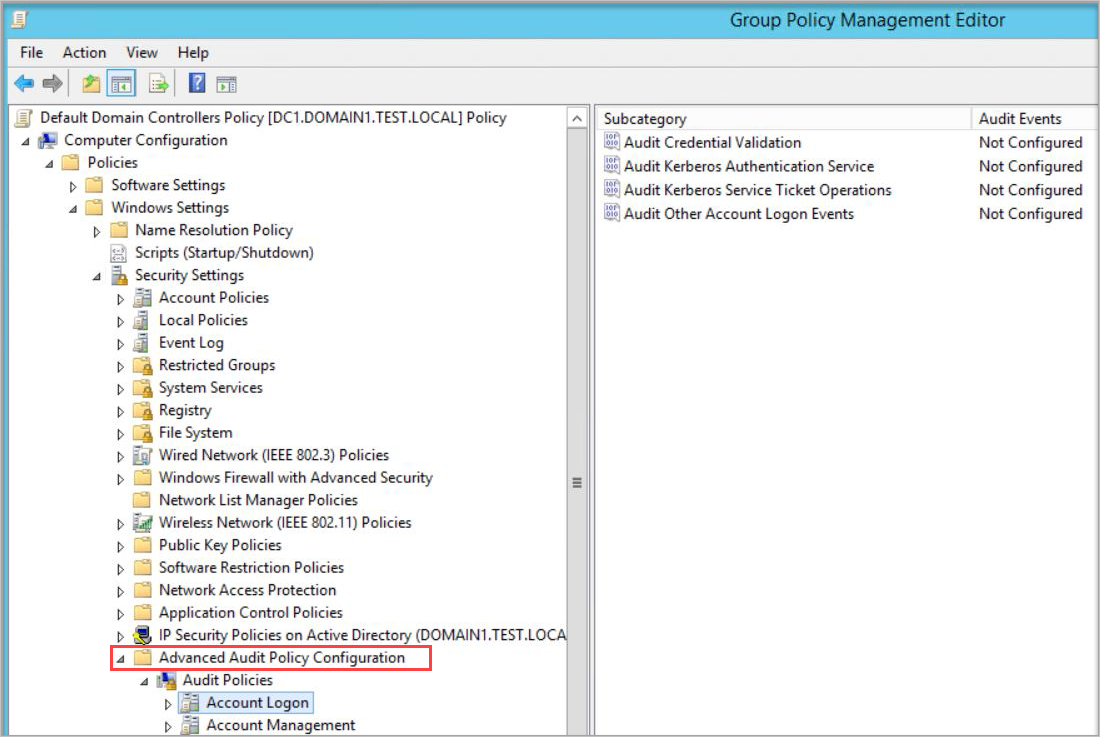
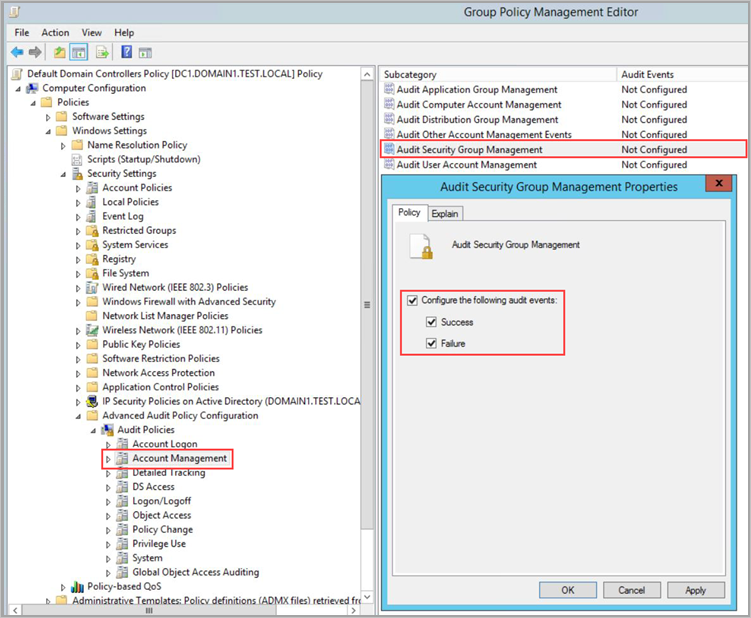
- Under Audit Policies, edit each of the following policies and select Configure the following audit events for both Success and Failure events.
Audit policy Subcategory Triggers event IDs Account Logon Audit Credential Validation 4776 Account Management Audit Computer Account Management 4741, 4743 Account Management Audit Distribution Group Management 4753, 4763 Account Management Audit Security Group Management 4728, 4729, 4730, 4732, 4733, 4756, 4757, 4758 Account Management Audit User Account Management 4726 DS Access Audit Directory Service Access 4662 – For this event, it’s also necessary to Configure object auditing. DS Access Audit Directory Service Changes 5136 System Audit Security System Extension 7045 For example, to configure Audit Security Group Management, under Account Management, double-click Audit Security Group Management, and then select Configure the following audit events for both Success and Failure events.
- Go to Advanced Audit Policy Configuration > Audit Policies.
- From an elevated command prompt type
gpupdate. - After applying via GPO, the new events are visible in the Event Viewer, under Windows Logs -> Security.
Event ID 8004
To audit Event ID 8004, additional configuration steps are required.
- Following the initial steps mentioned above, open Group Policy Management and navigate to the Default Domain Controllers Policy.
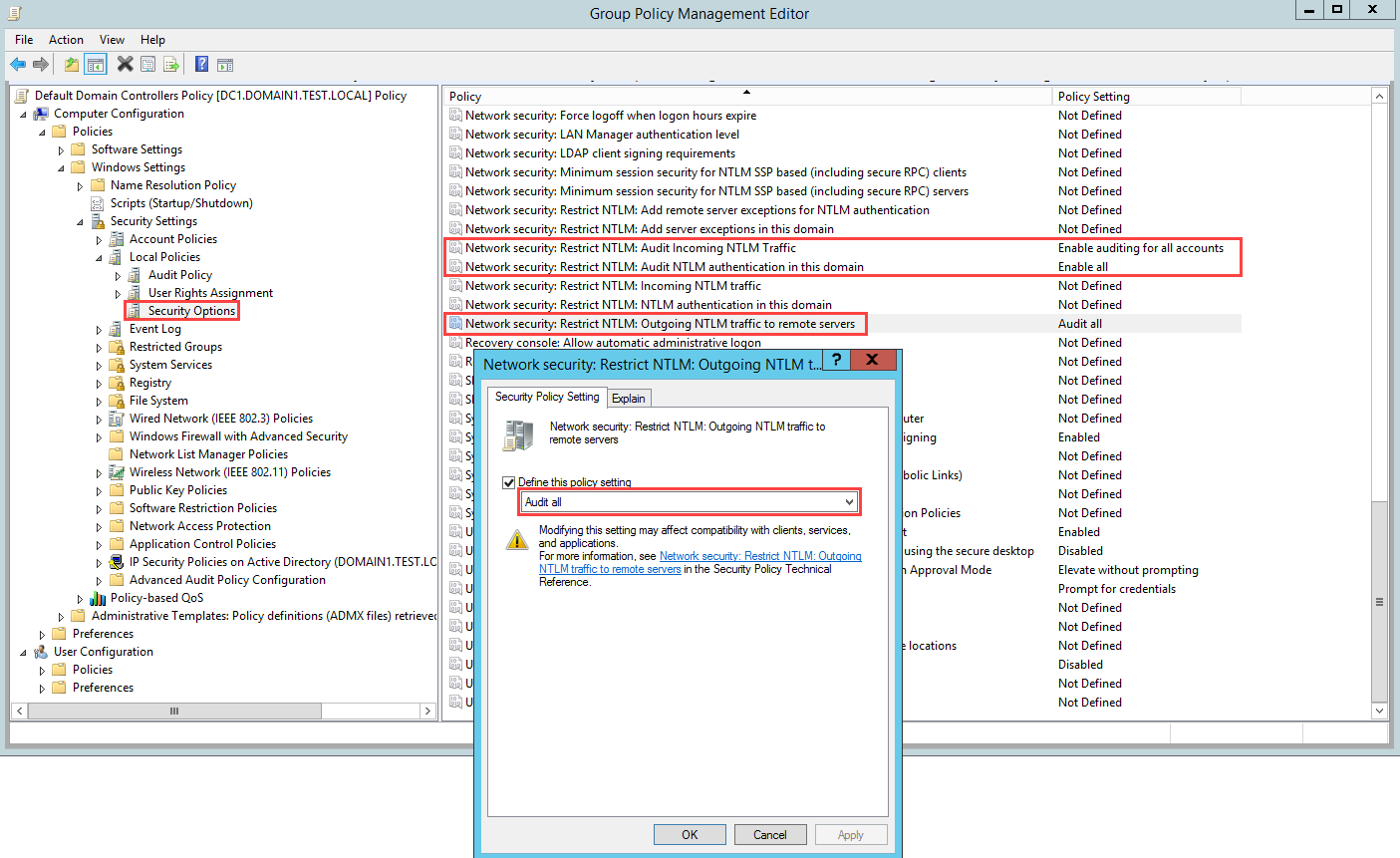
- Go to Local Policies > Security Options.
- Under Security Options, configure the specified security policies, as follows
Security policy setting Value Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers Audit all Network security: Restrict NTLM: Audit NTLM authentication in this domain Enable all Network security: Restrict NTLM: Audit Incoming NTLM Traffic Enable auditing for all accounts For example, to configure Outgoing NTLM traffic to remote servers, under Security Options, double-click Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers, and then select Audit all.
Cheers!
-Trevor